Secure managed services


Advanced cyber security
Back up and DR
Modern business landscape values the “always-on” principle, which means that a company should be ready to deliver services or goods to the customer at any time, despite the circumstances. However, when it comes to VMs with business-critical systems and apps, they should be a part of your disaster recovery planning. This does not only ensure business continuity but can also help you protect your company’s critical data in case of disaster.
Remote Management and Monitoring

About
Managed Security Service Provider MSSP
With an ever-evolving cyber landscape, businesses are facing increased and more complex threats to their environments. Attacks are happening at a far greater rate and the damage they pose is immeasurable. From data breaches, to insider threats, to ransomware attacks, the list is endless. As a result, many companies find themselves navigating through little understood waters without the right equipment, or knowledge at their disposal. The fall out is that these organisations become victims to truly damaging attacks, costing them both in revenue and reputation.
Managed Security Services
As a government accredited Managed Security Service Provider (MSSP), GGG Technologies helps UK organisations of all sizes build cyber-security capabilities and maintain compliance through practical consulting and managed services. Our unique security standing means we monitor highly regulated government networks, we take this capability and apply the same level of service to all our clients across the board, giving them the highest level of protection and ultimate peace of mind.
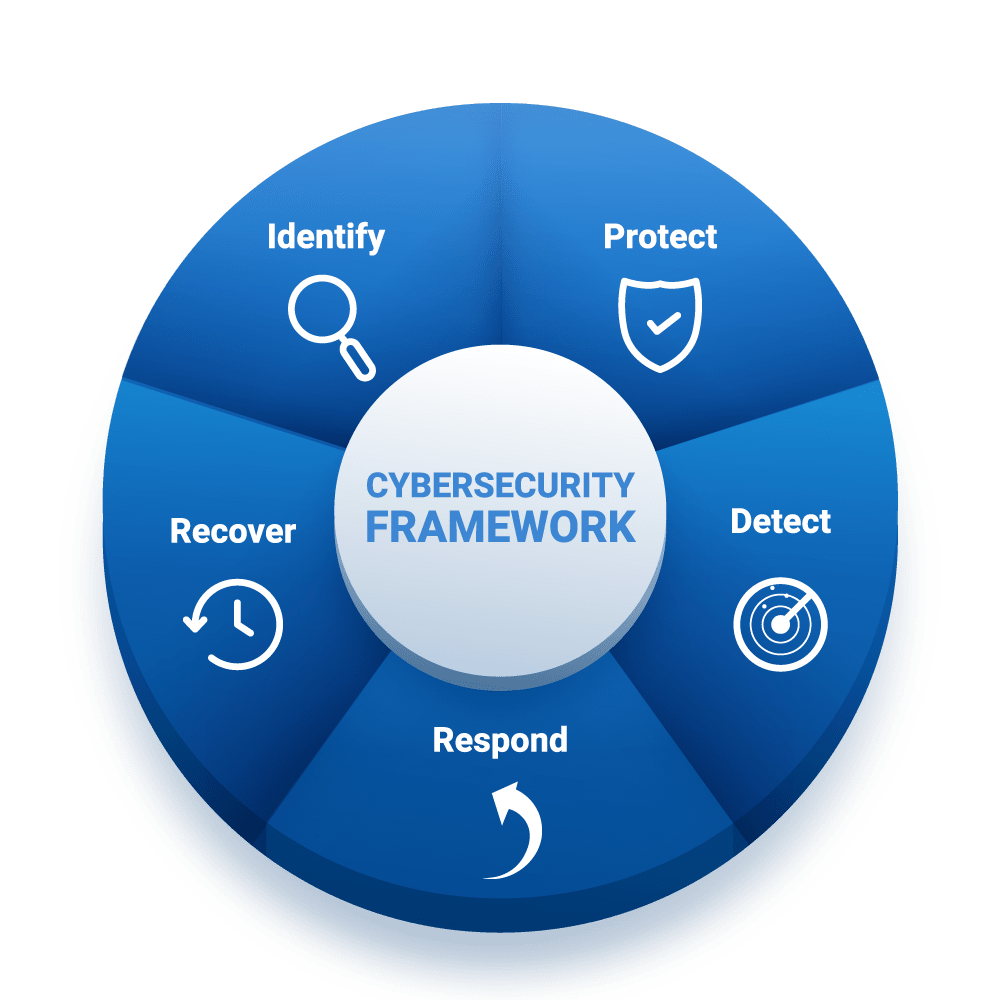
Features
What We Offer
Threat Management
Donec sollicitudin molestie malesuada. Vivamus magna justo, lacinia eget consectetur sed
Vulnerability Management
Donec sollicitudin molestie malesuada. Vivamus magna justo, lacinia eget consectetur sed
Incident Response
Donec sollicitudin molestie malesuada. Vivamus magna justo, lacinia eget consectetur sed
Approach
Our Approach to Security
Superior threat intelligence and advanced analytics, protecting, and optimizing your organization
Turn data into knowledge and see your entire security picture, rather than isolated events. Our Managed Security Services (MSS) leverage investment in threat intelligence and advanced analytics. Feeding into a purpose-built platform, it provides best-of-breed capability to deliver a diverse array of Managed Security Services. Our supporting security experts deliver transparent and repeatable services, identifying and stopping advanced threats. Furthermore, providing insight and metrics into security posture and trends.
Web Application Firewall-as-a-Service
Our Web Application Firewall as a Service provides the expertise and skills that ensure your web application firewall (WAF) is configured to provide the highest level of protection for your websites. The service provides detection of cyber threats, DDoS protection, business and regulatory compliance reporting.

Contact Us
+44 20 3642 4958
86-90 Paul Street London EC2A 4NE, United Kingdom
Monday-Friday: 8am – 5pm
Get Started
We know that clients want expertise, a service they can rely on and intimate support from a named individual who knows their business. It goes beyond technology.
Proactive cyber defence and detection
Our proactive cyber defence and detection services
Managed Cyber Defence
Our 24×7 service leverages best of breed technology merged with our threat intelligence, skilled threat hunters and advanced security orchestration and automation platform (SOAR).
We give you confidence that your business operations will remain resilient while freeing up your cyber team to focus on improving your security posture.
Ethical hacking
By replicating the latest techniques used by cyber criminals, we help you understand your security vulnerabilities, assess your ability to detect and respond to a cyber attack, and create a remediation plan to reduce your risk exposure.
Cyber threat intelligence
We can give you visibility of global threats, provide technical details on new and innovative attacks, and enable you to make strategic decisions based on a clear understanding of cyber threats.
Cyber incident response and recovery
Our cyber incident response practice can advise organisations who are preparing for, responding to and learning from cyber security incidents to help minimise business impact and residual risk.
Endpoint monitoring
By combining rich data collected by Tanium with external data sources and advanced models, we also provide a risk modelling service that identifies high risk threats vectors in your IT estate. Our interactive dashboards give a comprehensive view of your organisation’s vulnerabilities and enables you to track progress over time.
Identity and Access Management
We can help with all IAM business challenges, including supporting your digital transformation, securing and governing access, enabling a seamless customer experience, and advising on more effective risk-based governance.
Software security and DevSecOps

